This feels like one of those subjects that most people are unaware of, but given the increasing use of wi-fi in public places, and how easy it is for criminals to intercept traffic, it’s definitely one to be aware of.
The real-world threats that exist when you use “free” or open wi-fi in a hotel, café, station, airport or any other public place seem to be much less discussed in the mainstream press than things like running antivirus software. But the risks of allowing your traffic to be seen in a public wi-fi environment are, if anything, much greater.
Let’s take a look at the two main concerns when using public wi-fi:
- Fake wi-fi networks looking like genuine ones, and
- Genuine but open wi-fi networks
Fake wi-fi networks looking like genuine ones
Most of us will have used public wi-fi hotspots over the past few years. They’re convenient if you’re low on mobile data with your airtime plan, or coverage is non-existent, or simply if your 3G or 4G connection is really slow.
Typically we use wi-fi like this in cafes, bars, restaurants, airports, stations – even large department stores and supermarkets. Those networks might be provided by the businesses themselves, or by companies dedicated to providing public wi-fi like The Cloud, Boingo and others, or our own Internet Service Provider e.g. BT, Sky, Comcast etc.
Pull up a cuppa …
So you’ve just sat down in the new place to go in town, the Mange Tout Café, with your morning croissant and flat white, and you look around to see on the blackboard that the wi-fi network is called “MANGE_TOUT_CAFE” and there’s no password.
You open up your wi-fi settings on your phone and see the following:
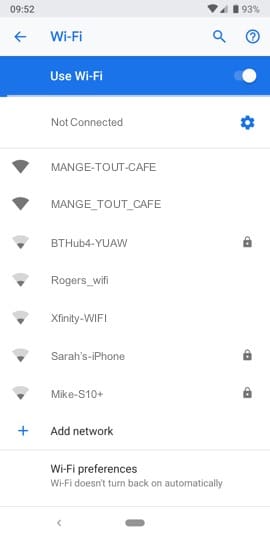
The question is, which one do you pick? They both have really good, strong signal and neither of them has the padlock next to them, so you know they’re open.
There’s a long line of people waiting at the till, so you don’t want to bother the staff either by asking a question or by pointing-out that there are, in fact, two “MANGE_TOUT_CAFE” networks.
So you plough on and connect to one of them. They’re the same, right, and that’s what the blackboard says…?
Many of you will already have spotted that, actually, only one of them is the genuine “MANGE_TOUT_CAFE” network, with underscores between the words – the other has hyphens. But in a busy café, with the name of the network written by hand in chalk on a blackboard, you could easily fall into the trap of connecting to the wrong one.
Some fake networks are not as obvious as that one. It could easily have looked like this …
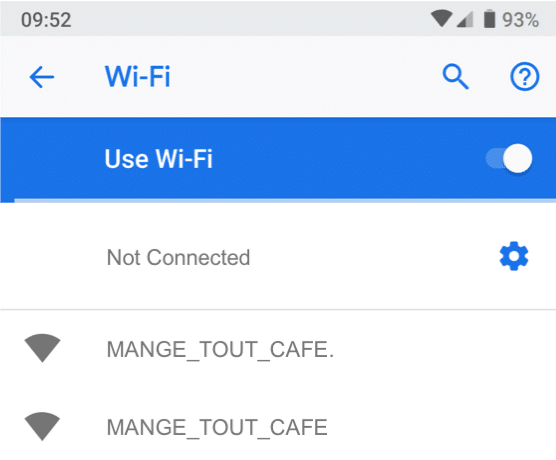
Either way, if you connect to the genuine network, you’ll be connecting to the white D-Link-branded box mounted on a bracket high-up on the café wall that the owners put there when they opened it a few weeks ago.
Connecting to “MANGE-TOUT-CAFE.” means that your signal is actually going over to the quiet, bookish-type lady in the corner and into the Lenovo laptop she’s using. She’s not browsing the news or working on a spreadsheet. What she’s doing is syphoning off all the data from every connection made to the fake network in the café, so that if anyone logs into unencrypted online shopping or social media accounts, for example, she has their usernames and passwords safely tucked-away either to use later, or to sell on to the highest bidder.
You’re quite happily surfing away none-the-wiser – you have a good, strong, fast internet connection doing what you need to get done, but all the while everything you see and everything you type could be going straight to the quiet criminal sitting across from you in the café.
The first you’ll know of it could be days, weeks or even months later when your online accounts are compromised and either you are locked out, or you find that someone has been draining your bank account, or buying themselves loads of gifts on your online shopping account. Either way, it’s highly unlikely that you’ll think back to your visit to the café and see that as the cause of the trouble you’re now experiencing.
Genuine but open public wi-fi networks
You won’t be surprised to hear that the way your data can be intercepted, read and stored when accessing an open public wi-fi network is much the same.
If you are using an open, un-encrypted connection, in theory anyone, with the right skill and equipment could hack their way into that connection and syphon off all the data passing through it.
Once again, you would have no idea in real-time that it was happening, and the consequences may not be felt for some weeks or months.
Encryption is your best way of protecting yourself – get a VPN
Whether you accidentally connect to a fake network, or you use a genuine, but open and un-encrypted public wi-fi network, the best way to protect yourself is to scramble (encrypt) all the data you send and receive by using a Virtual Private Network (VPN). That can take the form of an app on your phone or tablet, or a program on your laptop – all the major, trusted software VPN providers offer access to their services whatever device you’re using and you can find a selection of established, reputable VPN providers here.
You can set most of those VPNs to come on automatically when they detect an un-known or public wi-fi network. You can even set them to block sending or receiving any internet traffic via wi-fi unless you have activated a VPN connection. The latter can result in you finding that you unexpectedly look like you have no access to an internet connection at all – so unless you remember to go into the VPN app and manually open-up a connection, you might get frustrated at seemingly not being able to connect. In some ways, switching both those automatic protections on might be a bit intrusive, although it would give you the best possible protection against your data “leaking” out if your phone decides to connect automatically to a wi-fi network it’s seen before.
The point with VPN software is that it is relatively straightforward and cheap to guard against either an innocent mistake (connecting to a fake network) or unwanted intrusion (having your wi-fi connection hacked) coming back and hitting you unexpectedly in the future.
This kind of criminal activity is becoming ever more prevalent as the availability, and our use of, public wi-fi continues to increase.
It’s another example of how important it is to understand and choose whether to respond to the risks that the increased convenience of being “always connected” brings.


